Microsoft Defender for Identity
Active Directory (AD) is still at the heart of most businesses today. Although being very critical, it also offers a large attack surface for any potential attacker. This is why a lot of cyber attacks have shifted to identity based attacks, as they offer the most bang for the buck. These attacks may lead to a security breach and cause significant damage to an organization.
Recently many security solutions have become available that can protect AD from these advanced threats. One such solution comes from Microsoft and is called Defender for Identity (MDI). MDI uses on-premises agents installed on your domain controllers in order to send logs and analytics about critical activity occurring in AD. This data is sent to the Microsoft cloud, which in turn uses known threat patterns and machine learning to detect anomalous behavior. Some of these advanced threats that MDI can detect are:
- Account enumeration reconnaissance
- pass-the-hash attack
- Suspicious VPN connection
- Remote code execution attempt
- …
You can find the full list of detections on the official website here: Microsoft Defender for Identity security alert guide | Microsoft Docs
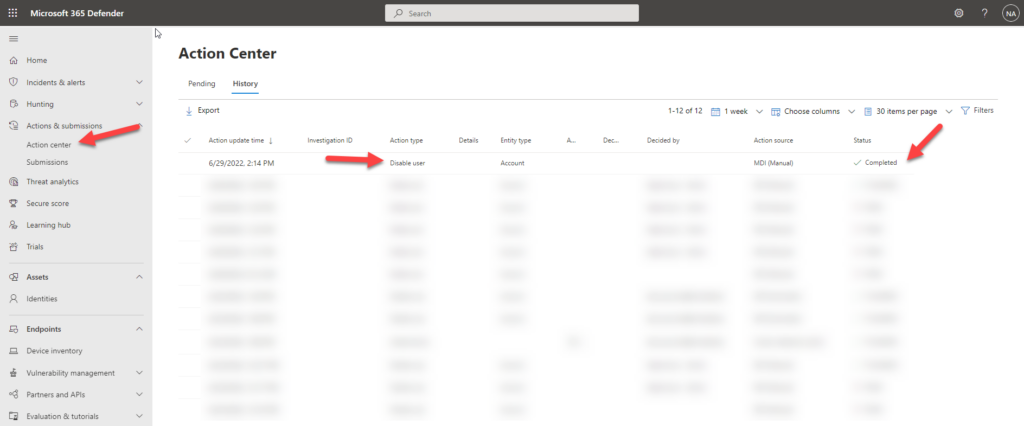
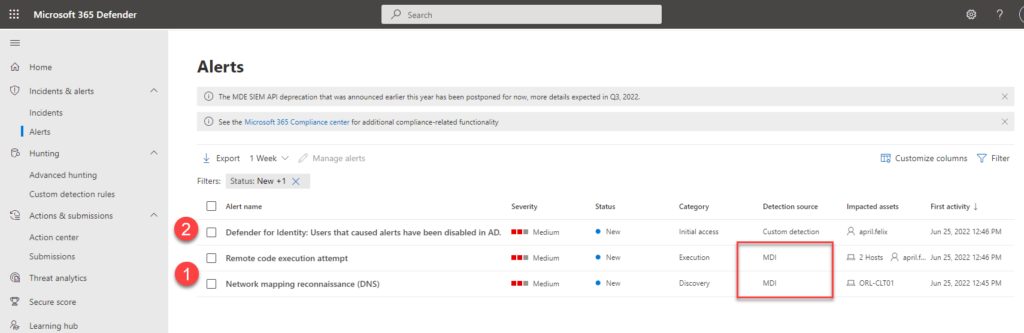
Despite the fact that this solution provides excellent visibility into advanced AD threats, it currently only generates alerts and notifications when such threats occur. So whenever a threat was detected, a potential SOC team had to manually contain these threats, for instance by disabling or resetting passwords of the affected accounts to prevent lateral movement.
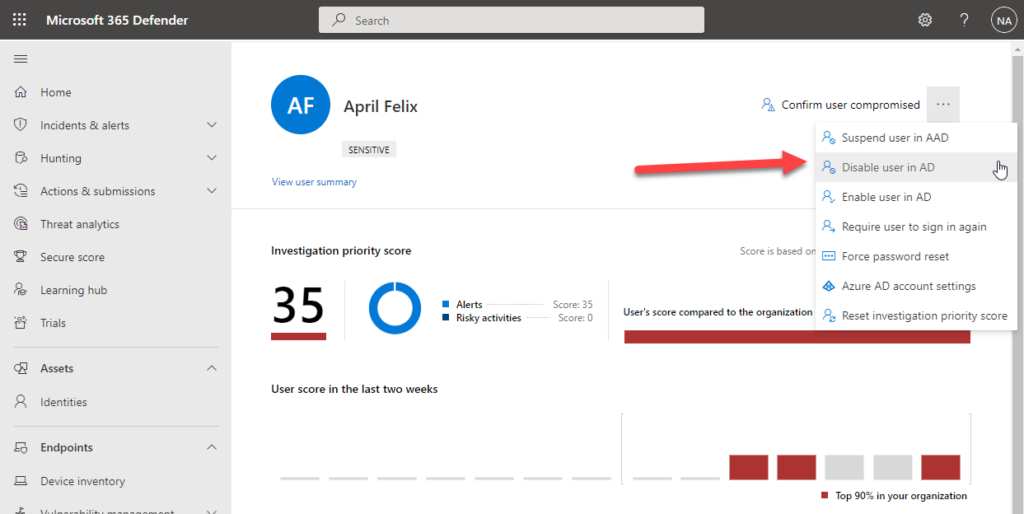
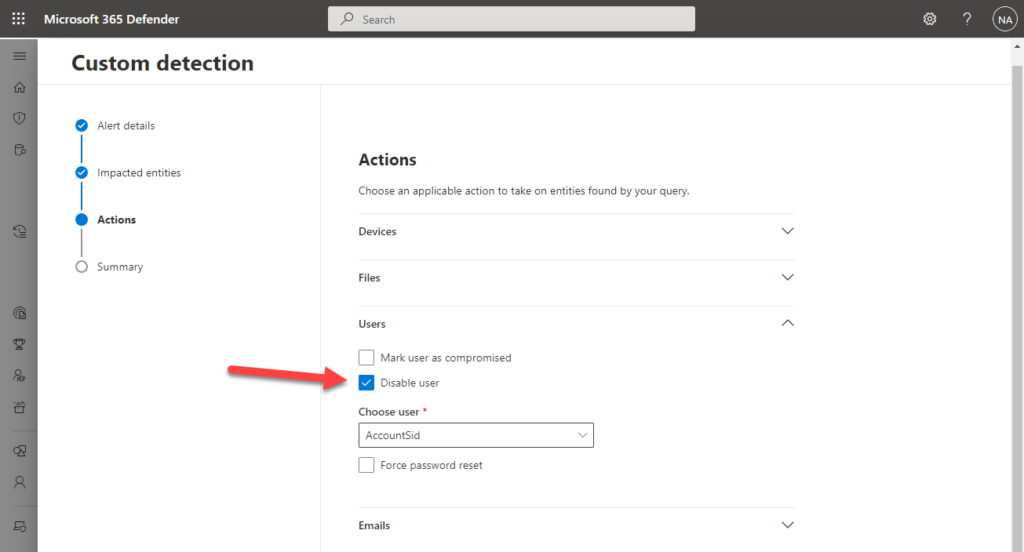
However this limitation has recently changed as MDI now offers the possibility to perform actions on an AD account. These actions are:
- Disable User
- Reset user password
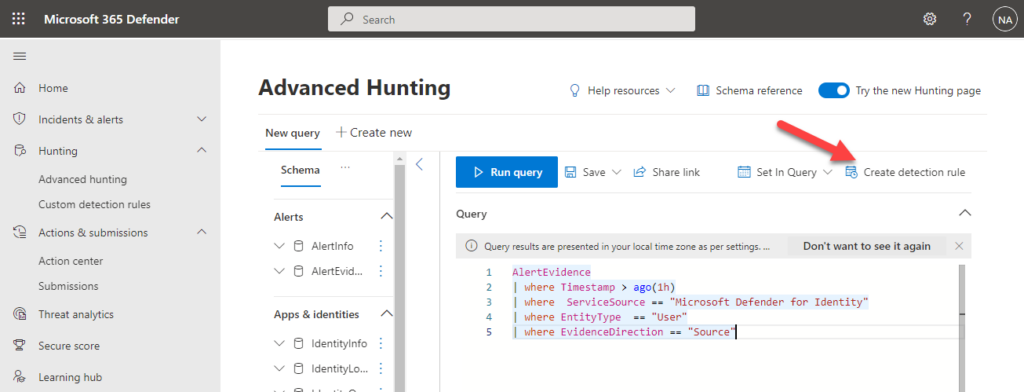
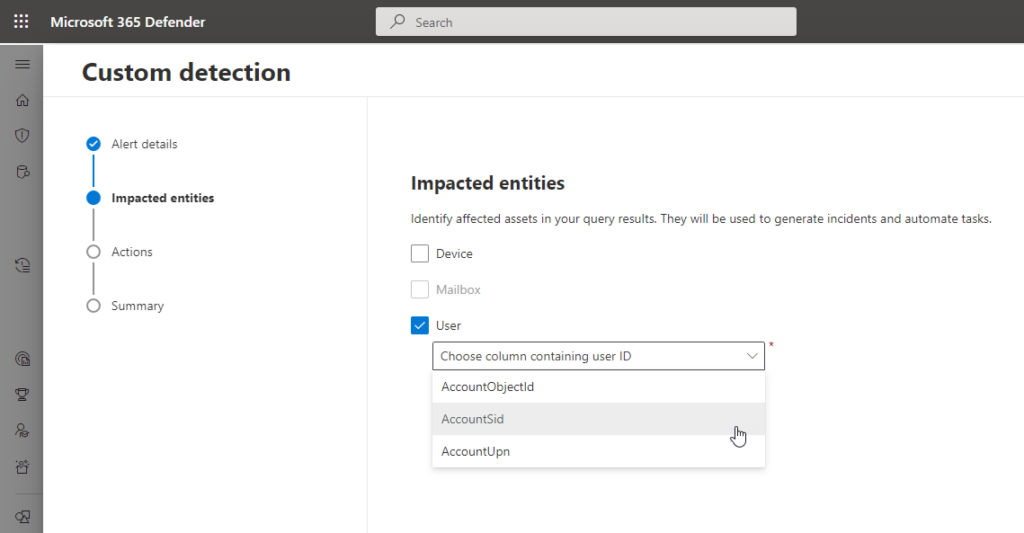
These actions can be performed from the Microsoft 365 Defender portal either manually or automatically using custom detection rules, which we will explore further below.